Lorem ipsum
Penetration Test
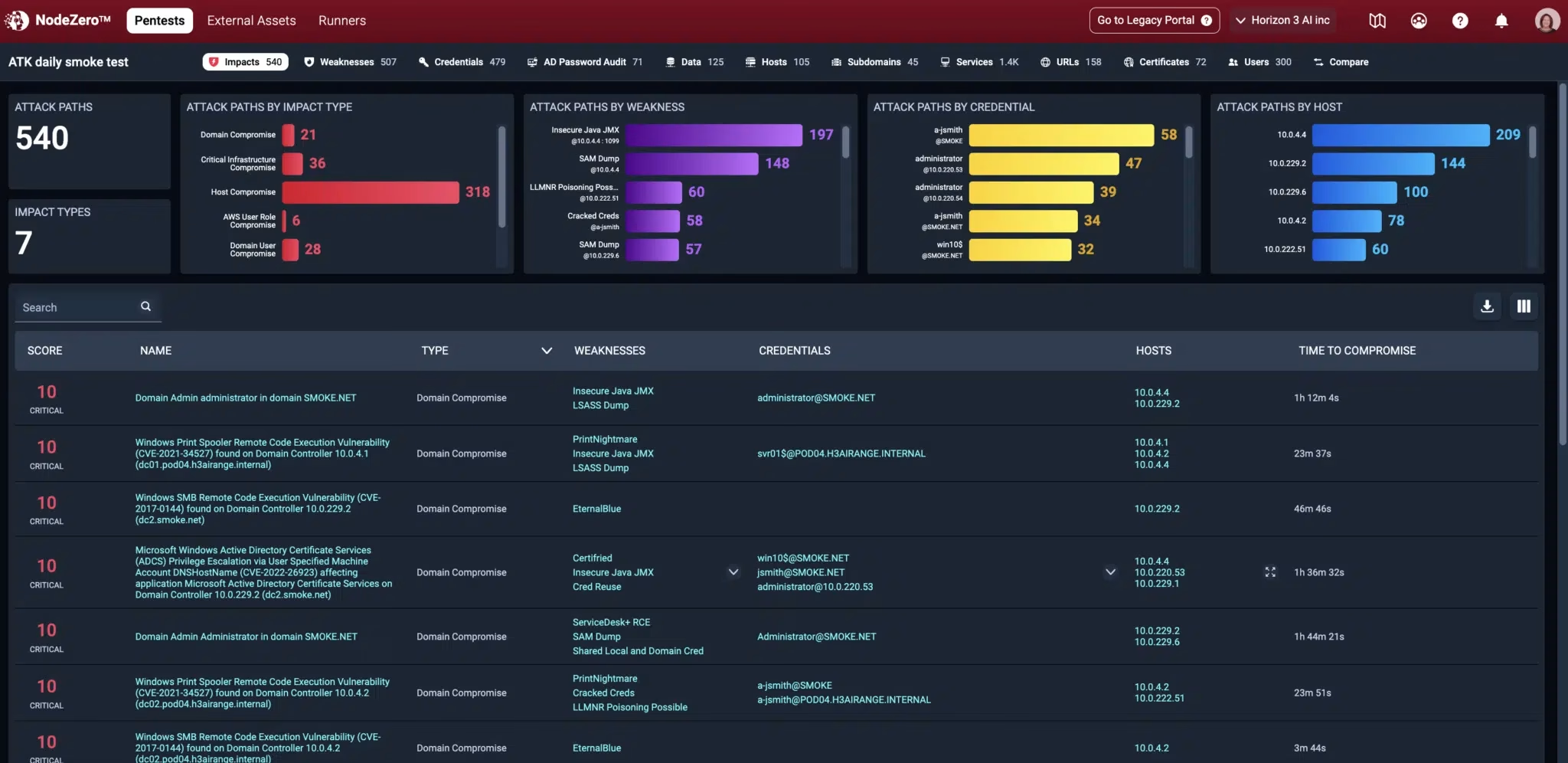
Our Penetration Testing service goes beyond automated scans by simulating real-world attacks to uncover hidden vulnerabilities in your systems before malicious actors do. Conducted by certified ethical hackers, our tests are tailored to your unique infrastructure—whether cloud, on-premises, or hybrid—and deliver actionable insights, not just generic reports.
We don’t just find weaknesses; we help you fix them fast with prioritized recommendations, boosting your security posture and compliance with standards like ISO 27001, PCI-DSS, and NIST. Partner with us to turn your cybersecurity into a strategic advantage.